46% of Medical IoT Devices Have a Vulnerability, a New Study Reveals
April 17, 2023
For 53% of institutions, breaches in connected systems affect patients—e.g., lead to delayed surgeries or transfers to other facilities.
Types of IoT devices
In the pursuit of personalized care, medical organizations are adopting IoT devices to collect health-critical information in real time and improve the quality of treatment. A February 2023 report from Cynerio revealed that the most popular types of connected device in hospitals are IV pumps, patients monitors, and glucometers.
More institutions are integrating the readings from remote patient monitoring equipment with centralized medical systems. According to a November 2022 study by CHiME, almost 90% of organizations send EKG information directly to an electronic health records (EHR) system. Additionally, 80% upload blood pressure information, and 76% integrate medication dispensing information. The research also shows that 51% of healthcare organizations integrate wearables data with EHRs.
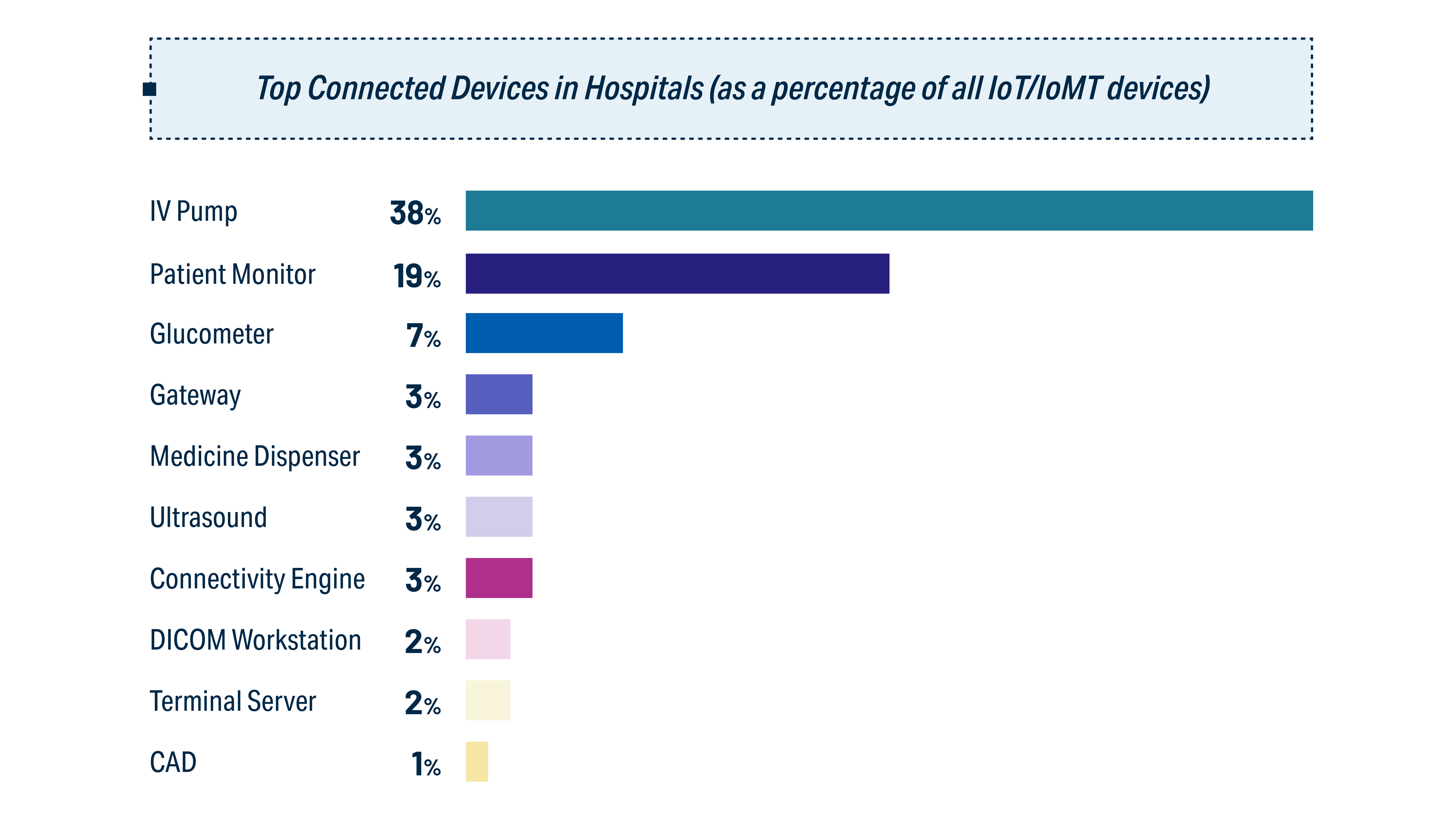 Most common types of IoT devices in a hospital (image credit)
Most common types of IoT devices in a hospital (image credit)At the same time, medical IoT devices use a variety of operating systems. CHiME indicates that Linux is by far the most popular, with a 46% share. However, more than half of devices use a variety of heterogeneous proprietary platforms, as well as outdated ones, such as Windows CE. In general, 82% of respondents in a Capterra survey (2022) noted medical devices running an operating system from Microsoft older than Windows 10.
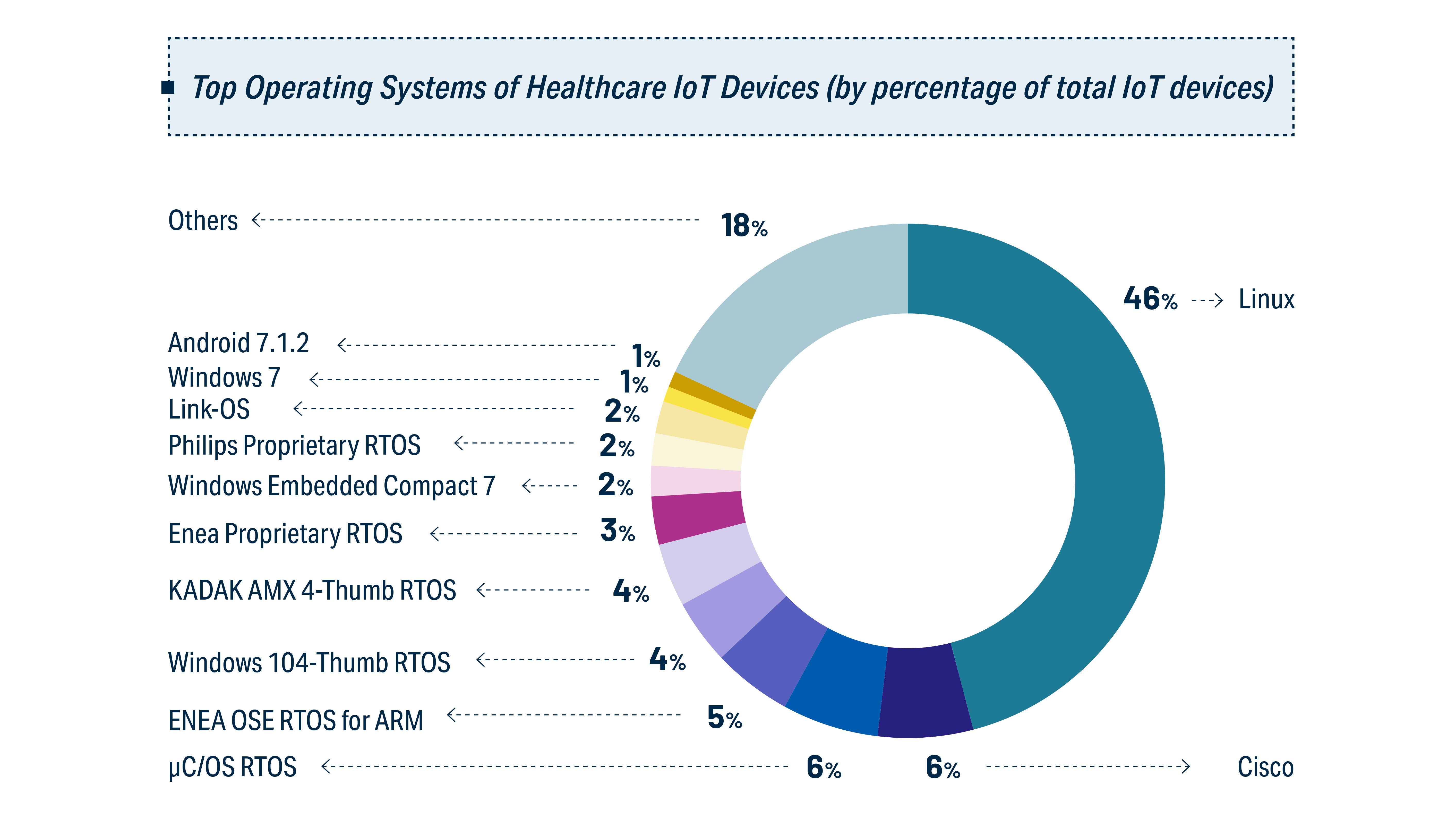 The variety of operating systems used in medical IoT devices (image credit)
The variety of operating systems used in medical IoT devices (image credit)As the use of robotics, sensors, and digital technologies continue to grow, new opportunities for exploitation emerge. A February 2023 report from Health-ISAC found that hospitals with a higher number of connected medical devices faced more cyberattacks and had increased chances of multiple incidents.
This article explores the most common types of vulnerabilities, sheds some light on what to expect in 2023, as well as provides recommendations from IoT security experts.
Types of vulnerabilities to look out for
In April 2022, five software glitches were found in the firmware of TUG robots used by a range of US hospitals. These could enable criminals to control the machines, as well as lock doors and elevators, creating threats to patients and staff. Attackers could also gain access to medical documents, surveillance footage, and spread the malware to other devices by taking over administrative sessions in the robots’ online portal. Although the issue was patched quickly, other vulnerabilities may still be undiscovered.
Unfortunately, some IT security issues lead to more severe consequences. In February 2023, a cyberattack on the Tallahassee Memorial Hospital in Florida forced the organization to shut down its entire computer system. As a result, the institutions had to send emergency patients to other facilities and cancel some nonemergency surgeries.
The integration of IoT devices has increased the exposure of healthcare to cybersecurity risks. A February 2023 study by Cynerio showed that 46% of medical devices had an unaddressed vulnerability. Furthermore, 11.7% of devices had at least one critical risk. Consequently, healthcare organizations with a higher percentage of connected medical devices are more vulnerable to cyberattacks.
One reason for these vulnerabilities is that healthcare organizations often fail to implement basic security measures. In Capterra’s report, only 43% of respondents said they changed default passwords on IoT medical devices, and just 32% applied the latest updates.
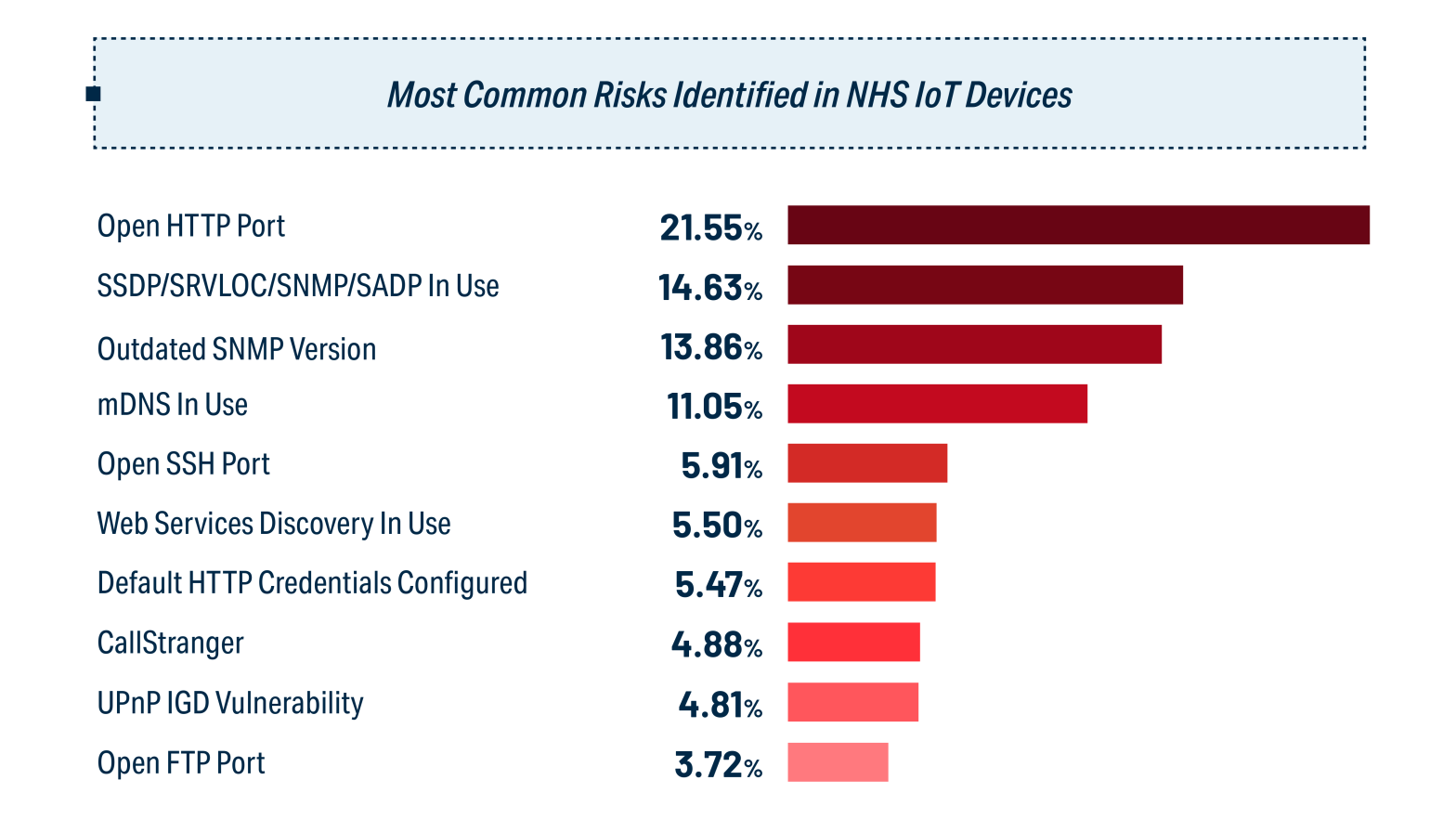
 Common medical IoT device vulnerabilities (image credit)
Common medical IoT device vulnerabilities (image credit)A January 2023 research paper by Nozomi Networks warns that the large number of vulnerable IoT devices that could be compromised remotely pose an additional challenge. One of the main ways attackers get access to IoT devices is the use of default credentials. Since many organizations neglect to set new passwords, threat actors can simply log in without needing to use exploits or social engineering.
The most common login–password combinations include:
nproc:nprocadmin:adminadmin:1234root:rootadmin:root:admin:passwordadmin:123456admin:12345user:user
Let’s explore how these gaps in security could be exploited by hackers.
Attacks to expect
A January 2023 report by Nozomi Networks and a study by Health-ISAC predict six types of attacks that healthcare organizations are likely to face this year:
- distributing ransomware
- DDoS attacks
- intercepting sensitive information during transmission
- abusing exploits in medical devices
- finding devices with weak/default login credentials
- creating synthetic accounts to circumvent security systems
The report from Nozomi Networks also notes that AI models, such as ChatGPT, could also pose security risks. This is because such systems allow even unskilled attackers to create malicious code or generate realistic-looking phishing e-mails.
Ransomware attacks are on the rise. A January 2023 survey by the Ponemon Institute found that 47% of medical organizations experienced a ransomware attack last year. Out of those attacked, 46% state that the breach was caused by a third party. Shockingly, the average ransom amount—paid by 67% of affected organizations—was a staggering $352,541.
For 53% of respondents, a ransomware attack affected patient care. 45% of organizations experienced complications from medical procedures due to ransomware attacks in 2022. The average disruption length measured 35 days.
Besides, 70% of respondents had to transfer patients to another facility because of an attack, and 68% said this increased their length of stay. Furthermore, delays in treatment resulted in poor medical outcomes for 58% of organizations, and 21% said that ransomware affected mortality rates. A report by Capterra also confirms these findings, discovering that 48% of healthcare cyberattacks impact patient care, and 67% affect personal data.
A February 2023 report by Health-ISAC (Information Sharing and Analysis Center) outlines a few potential attack vectors, as well. For instance, cybercriminals can use credential lists, which are freely available on many forums, to gain access to health records. Hackers also take advantage of compromised personal information to create synthetic accounts for bypassing identity checks, paying medical bills, stealing health data, etc.
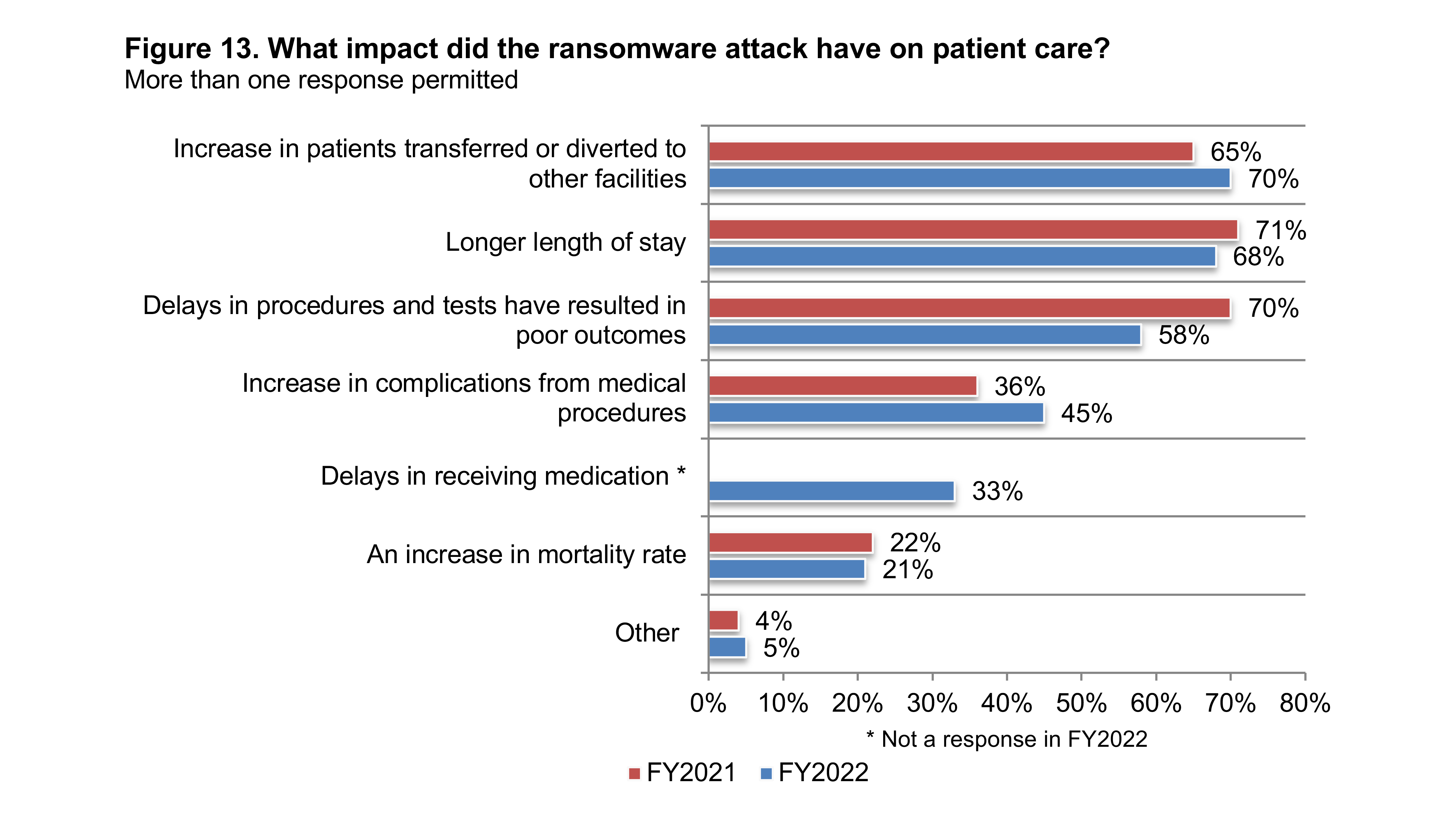 The effect of ransomware attacks on patient care (image credit)
The effect of ransomware attacks on patient care (image credit)Security recommendations
As cyberthreats continue to grow in frequency and sophistication, healthcare organizations must prioritize proactive defense strategies to protect their networks and data. Security is considered an essential or high-priority target for digital transformation in 2023, according to a CHiME report.
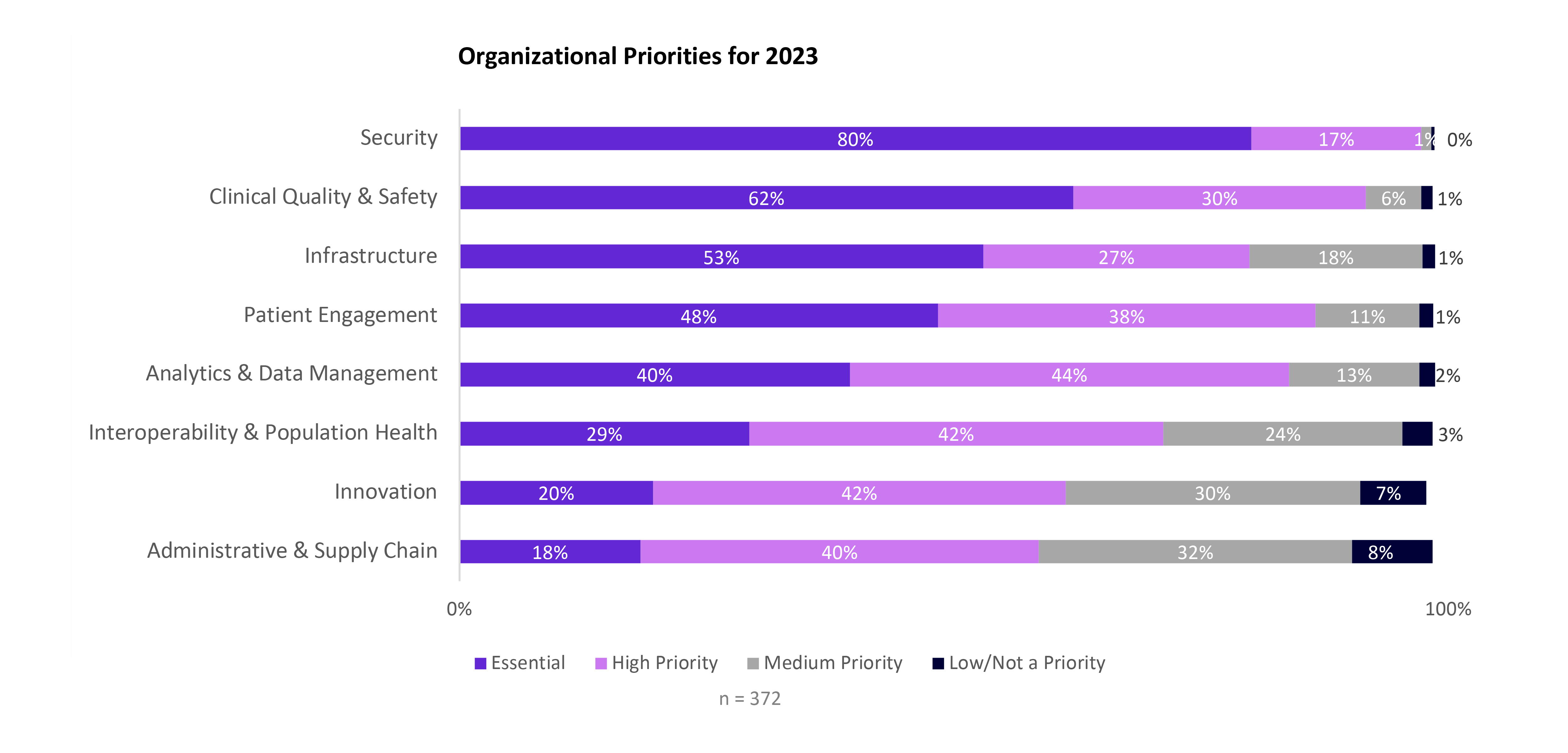 Priority in healthcare digital transformation (image credit)
Priority in healthcare digital transformation (image credit)Nozomi Networks recommends prioritizing network segmentation, asset discovery, vulnerability management, patching, logging, endpoint detection, and threat intelligence.
Health-ISAC suggests performing risk assessments and developing threat models to identify how devices may be susceptible to cyberattacks. The company also advises hospitals to change default or weak login credentials, and apply patches as soon as they become available. Engaging with caregivers to better understand the potential impact a breach can have on patient care is also essential.
Additionally, the Ponemon Institute provides some advice for protecting against ransomware attacks. With 46% stating that the intrusion was caused by a third party, it is crucial to have policies for assessing security of external systems (e.g., IoT devices), eliminating gaps, and recovering.
Finally, organizations must also be aware of threats to customer-facing products, which are routinely targeted by attacks designed to extract data. Capterra advocates for thorough monitoring of medical device data and traffic, along with aligned controls at the network, application, authentication, and risk layers. These measures should reduce the risk of credential stuffing, account takeovers, carding attacks, and synthetic account creation.
(Read how a medical software provider secured its spirometry/oximetry system with authentication token hashing, encryption, biometric sign-in, and controlling Bluetooth connectivity. Or, check out a story of a startup that produces blood sampling kits, which created a HIPAA-compliant IoT prototype involving barcode-scanning and temperature monitoring.)
To summarize, experts recommend medical organizations to take the following steps:
- always apply the latest updates and patches
- change default login credentials and strengthen passwords
- create policies for auditing third-party security
- establish processes for recovering after an attack with minimal disruption
- perform regular assessments to identify and patch vulnerable devices
- ensure traffic monitoring to reduce the risks from synthetic accounts
In conclusion, proactive defense strategies and threat modeling are indispensable for critical infrastructure and healthcare institutions. Since an attack on medical devices endangers people’s health, investing in robust security measures can eventually save human lives.
Frequently asked questions (FAQ)
-
What are the most common types of IoT devices used in hospitals?
Cynerio’s February 2023 report shows that the most popular types of medical IoT devices are IV pumps (used in 38% of hospitals), patients monitors (19%), and glucometers (7%). Healthcare organizations can also have medicine dispensers, ultrasound machines, as well as IoT gateways, robots, location-tracking systems, etc.
-
What are the potential consequences of a ransomware attack on medical IoT devices?
A January 2023 survey by the Ponemon Institute found that the average victim paid a $352,541 ransom and experienced a 35-day disruption. As a result, 70% of respondents had to transfer patients to another facility, and 68% said that it increased their length of stay. Furthermore, 58% of affected hospitals admitted that treatment delays worsened medical outcomes, and 21% reported an increase in mortality rates.
-
What are the most common ways attackers gain access to medical IoT devices?
A February 2023 paper by Cynerio indicates that 46% of medical devices have an unpatched vulnerability, and 11.7% have a critical one. According to a study by Capterra, only 43% of respondents change default login credentials on their devices, and just 32% apply the latest patches. Health-ISAC also warns hospitals that attackers could use stolen personal information to create synthetic accounts and deceive security systems.
-
How to protect medical IoT devices from cyberattacks?
Nozomi Networks suggests prioritizing network segmentation, vulnerability management, patching, logging, threat scanning, etc. Health-ISAC advises hospitals to perform risk assessments and identify how devices may be susceptible to cyberattacks. The Ponemon Institute urges hospitals to create policies for assessing security of third-party systems. Capterra recommends increased data and traffic monitoring, along with aligned controls at the network, application, authentication, and risk layers.
Further reading
- Stanford Hospital Speeds Up Care with IoT, AI, and Telehealth
- The Challenges of Implementing Data-Driven Personalized Healthcare
- The Challenges of Building a Remote Patient Monitoring System
Subscribe to new posts
Contact us and get a quote within 24 hours































